
In today’s time, every application needs authentication and authorization components. By using these approaches, one can limit or expand the user access to the system and also finalize the permissions to utilize the application and its modules. This becomes more essential for today’s applications that are designed with microservice architecture comprising many services. But when the software development team decides to authenticate and authorize the microservices application, questions like where and how to implement authentication or authorization or how to authorize the user actions come into their minds.
Therefore, in this blog, we will understand microservices authentication and authorization as well as we’ll go through the difference between Microservices authentication and authorization followed by some popular microservices approaches and techniques.
1. What is Microservices Authentication?
A microservices application is something that makes it possible to integrate several isolated services by using APIs. Before this interaction between microservices, the developers need to make sure that a microservice is authenticated. This type of authentication process will only enable authorized users and services to access each microservice. Besides this, in microservices, even users are authenticated. This prevents security holes.
2. Authentication vs Authorization
Generally, when it comes to securing an application in microservices, developers use a combination of authentication and authorization. Though both of these concepts are interchangeable, they have different purposes for securing an application. Here we will understand both these approaches to learn more about them and understand how both have different ways of protecting applications.
2.1 Authentication
Authentication is a process that enables the verification of the user’s identity in order to grant them access to the system. This process verifies that a particular user is who he/she claims to be. In order to confirm the identity of a user, successful authentication and a login is required.
2.2 Authorization
Authorization is a process that makes sure whether a particular user is authorized to access a particular set of data or to execute certain operations. In this process, the user’s permission is determined.
Basically, the combination of both these principles can be used in different ways to secure the application. To carry out them in an application, first, the developers have to authenticate login users of the application and then authorize the session data from users or other entities.
3. Microservices Authentication Approaches
When it comes to implementing an authentication strategy in a microservice application, any one of the following global authentication strategies can be used.
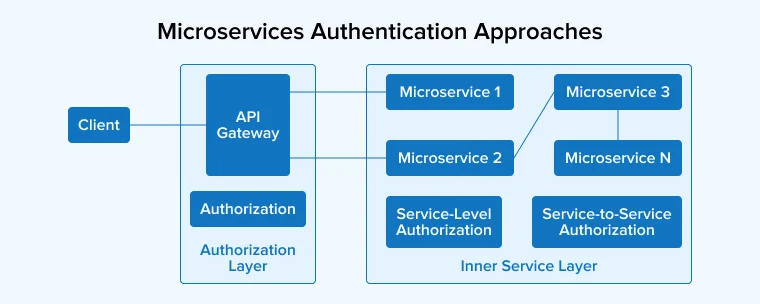
3.1 Service-Level Authorization
The very first approach for microservices is service-level authorization which enables direct authentication and authorization for each and every microservice present in the application. The main benefit of a microservice architecture using this strategy is that here each microservice will have more control to enforce its access control policies. A service-level authorization architecture comes with –
- Policy Administration Point: This point enables the administrators to create, manage, and test access rules of the application.
- Policy Enforcement Point: This point offers access decisions that eventually help in enforcing the access policy for specific types of client requests.
- Policy Decision Point: This point enables the developers to check which access control policy needs to be applied to the current request and whether to grant that request to the users or deny it.
- Policy Information Point: It enables the system elements to retrieve the policy data or receive account attributes that can help in making all the decisions regarding a policy.
3.2 Edge-Level Authorization
It is a very simple type of microservice authentication and authorization approach. As authorization is a process that can only occur at the edge with the use of an API gateway, that API Gateway can be used by the developers to centralize authentication and authorization for all microservices that are downstream. In this way, when the gateway enforces access control and authentication for each microservice, the implementation of mitigation control is carried out as per the recommendation of the NIST. This mitigation control can be mutual authentication between microservices and the reason behind it is to prevent direct anonymous connections to services, internally.
3.3 External Entity Identity Propagation
Another important strategy for microservice authentication is external entity identity propagation. This strategy enables the developers to make authorization decisions while looking after the user session context. Basically, in this approach, the developers will implement authorization but will also look at what the user wants. For instance, this method can help in changing the authorization decision that is based on user roles or groups, user ID, time, location, and more.
In order to perform such user authentication data based on the user context, the software development team must have proper information about the end user and then it can be propagated to downstream microservices. The developers can simply achieve this by taking the Access Token that is received at the edge and then transferring it to individual microservices. This is a type of approach that offers the most granular control to the development teams over microservice authentication.
4. Microservices Authentication Solutions/Techniques
After the software development teams decide which approach to use for authenticating their microservices application, the next step is to learn about technical methods of microservices authentication and see which technique they can implement in their solution.
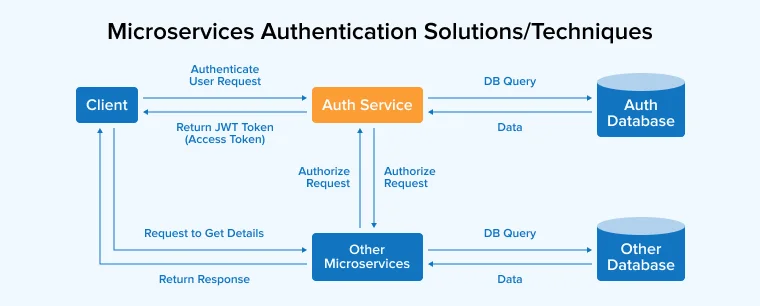
4.1 JSON Web Tokens
JSON Web Token (JWT) is one of the widely used microservice authentication solutions used by software development companies to offer a mechanism for sharing a set of properties or claims from the client to a microservices application in a very secure and encrypted manner. With the help of JSON Web Tokens, the developers can easily secure communication between end-user contexts or multiple services and data between microservices. For instance, a JSON Web Token can be used in an application to pass the ID of the calling services, ID of the system, or the client that wants to initiate the request. Then the authentication and authorization properties are saved in a JWT token and are shared between various servers and clients.
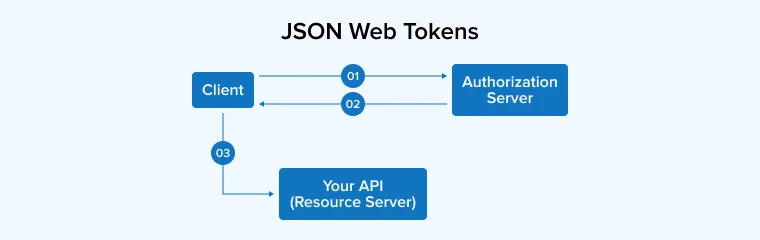
- The application or client requests authorization from the authorization server.
- When the authorization is granted, the authorization server returns an access token to the application.
- The application uses the access token to access a protected resource (like an API).
4.2 Single Sign-On (SSO)
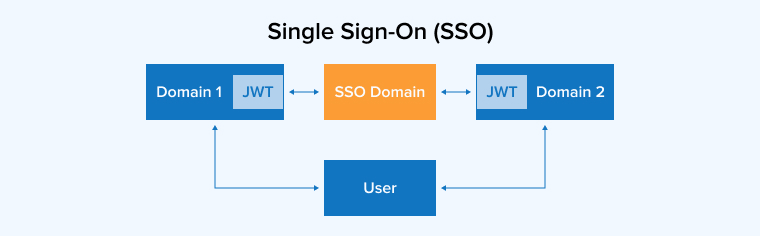
Another popular microservice authentication approach is SSO. This approach enables the users or any other entity to log in once in the service and gain access to various systems. When it comes to microservices architecture, Single Sign-On (SSO) can have two meanings and they are –
- End-users Authentication: Generally in any application, it is very convenient for the end-users to have central login which might enable them to use the existing credentials, instead of requiring new ones to log into the application. In such cases, one can use identity and access management (IAM) solutions to define permissions and set up a user database in a way that redirects the users to the IAM system for authentication, get the SSO token which is encrypted, and then allow them to log into the system. Basically, this approach restricts users’ false attempts to log into the microservice application when they want to and permits their access with proper protocols.
- Authentication of microservices: With this approach, the developers can enable SSO for microservices that require a connection with external services or other microservices via API. In this case, a software entity or service account is authorized with the same IAM solution. This makes the software entity ask for access when it wants to log into the system and at that time it will be redirected to the IAM. After the login request is sent to an IAM system, it will grant permission by offering an SSO token that can be used in future API calls.
4.3 OAuth API Authentication
The last microservice authentication technique in our list is OAuth API authentication. OAuth 2.0 comes with an industry-standard protocol that helps in authorizing users in distributed systems. When it comes to authenticating microservices, the client credential flow of OAuth 2.0 will support secure server-to-server communication between API servers and API clients. Besides this, the OAuth framework comes with the capability to lessen the burden of the software developers by removing the requirement to create an authentication method in API Gateway and other services. The developers can use OpenID Connect (OIDC) which will help in extending the OAuth API authentication service to add federated identities which will eventually help in setting up delegated authorization.
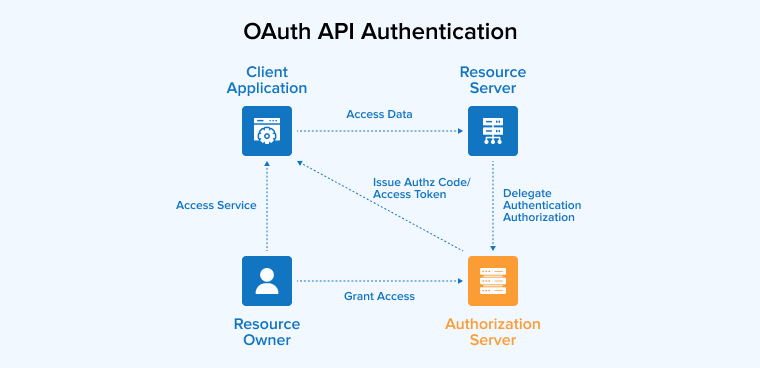
Both these layers can help the developers to create a stateless authentication system that can easily interact with various identity providers. This is why using OIDC with OAuth 2.0 is recommended as it will make it possible to even retrieve a user ID by sending an access token to the endpoint of the user information.
5. Conclusion
As seen in this blog, it can be difficult to deploy authentication and authorization into a microservices architecture. Both these approaches are used to protect an application. Authentication is required to verify the identity of an entity while authorization checks which access is granted to a particular entity. In a microservices architecture, both these methods are handled centrally but before authorizing anything, authentication is a must. This is why, in this blog, we had a deep dive into the microservers authentication approaches and techniques.




Comments
Leave a message...